Navigating Secure Connections: A Comprehensive Guide to SSH in Windows 11
Related Articles: Navigating Secure Connections: A Comprehensive Guide to SSH in Windows 11
Introduction
With great pleasure, we will explore the intriguing topic related to Navigating Secure Connections: A Comprehensive Guide to SSH in Windows 11. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating Secure Connections: A Comprehensive Guide to SSH in Windows 11
Secure Shell (SSH) is a vital tool for securely connecting to remote systems, enabling users to manage, access, and interact with these systems over a network. Windows 11 offers robust SSH capabilities, simplifying the process of establishing secure connections and streamlining remote administration tasks.
Understanding the Foundations: SSH and Public-Key Authentication
SSH employs public-key cryptography, a fundamental security mechanism that allows secure communication without relying on passwords. This system revolves around two keys: a public key and a private key. The public key is freely distributed, while the private key remains securely stored on the user’s device.
Public-key authentication leverages these keys to verify the identity of a user attempting to access a remote system. When a user attempts to connect via SSH, their public key is presented to the remote server. If the server has a copy of this public key stored in its authorized keys file, it confirms the user’s identity and grants access. This eliminates the need for passwords, enhancing security by preventing unauthorized access.
The Role of ssh-copy-id in Windows 11
The ssh-copy-id utility simplifies the process of adding a user’s public key to a remote server’s authorized keys file. This utility streamlines the setup of secure connections, eliminating the manual steps of generating, transferring, and adding the public key.
Key Benefits of Using ssh-copy-id
-
Enhanced Security: By eliminating password-based authentication,
ssh-copy-idstrengthens security by preventing unauthorized access. - Streamlined Setup: This utility automates the key management process, simplifying the configuration of secure connections.
-
Increased Efficiency:
ssh-copy-idreduces the time and effort required to establish secure connections, allowing users to focus on their tasks.
Practical Implementation: Setting Up SSH Connections with ssh-copy-id
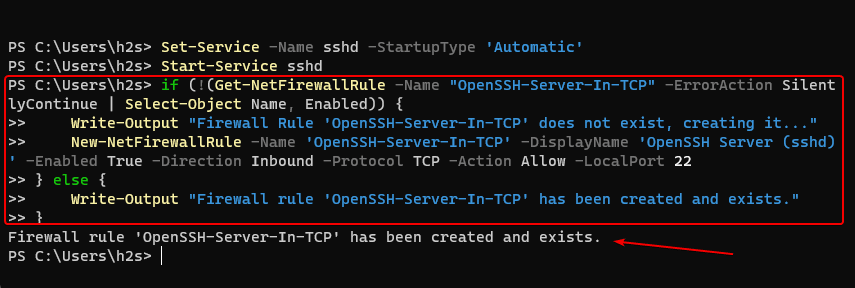
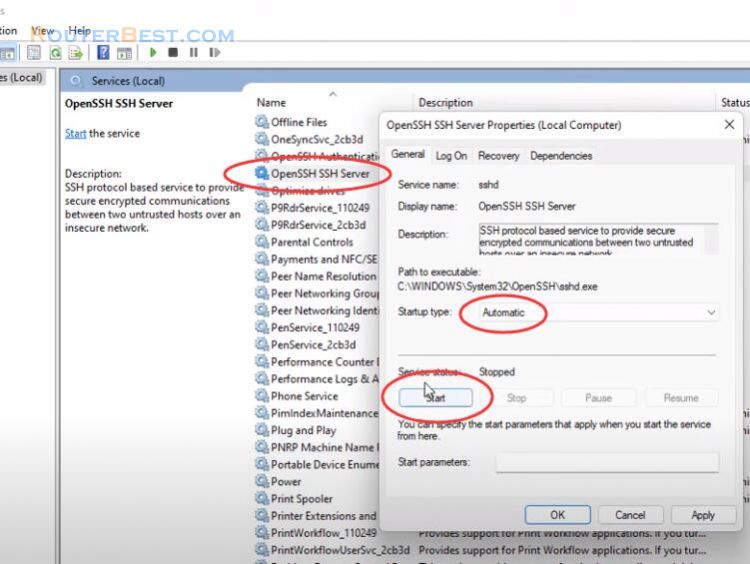
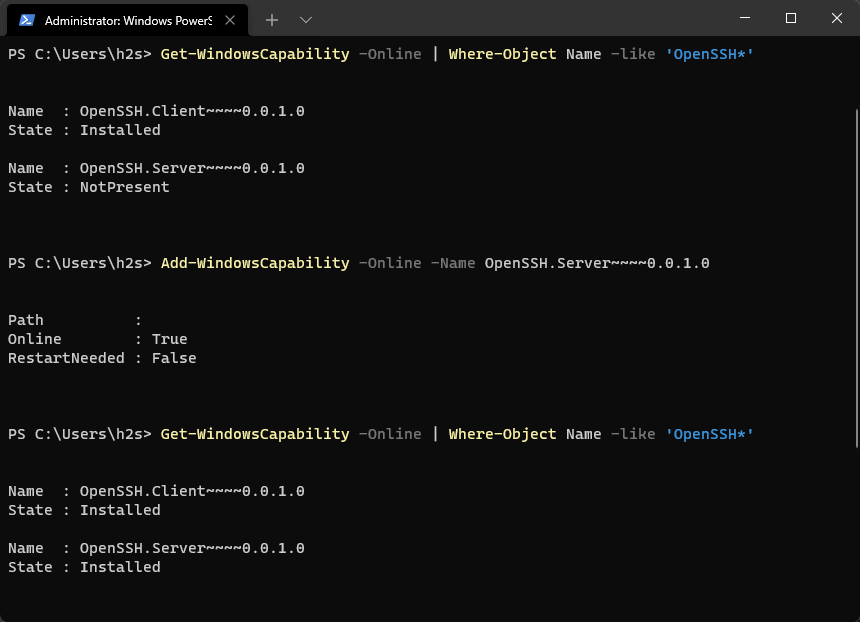
- Enabling SSH Server on the Remote System: Ensure that the remote system has an SSH server installed and configured. This is typically achieved through packages like OpenSSH or similar server software.
-
Generating an SSH Key Pair: If you haven’t already, use the
ssh-keygencommand to generate an SSH key pair. This will create a public key and a private key. -
Using
ssh-copy-id: Run thessh-copy-idcommand with the username and hostname of the remote system. This command will securely transfer your public key to the remote server and add it to the authorized keys file. -
Testing the Connection: After successfully running
ssh-copy-id, attempt to connect to the remote system using SSH. You should now be able to access the server without entering a password.
Example:
ssh-copy-id [email protected]FAQs
Q: What if I encounter errors while using ssh-copy-id?
A: Errors can occur due to various factors, such as incorrect usernames, hostnames, or network connectivity issues. Carefully review the error message and consult relevant documentation or online resources for troubleshooting steps.
Q: Is it necessary to use ssh-copy-id for secure connections?
A: While ssh-copy-id simplifies the process, it is not strictly necessary. You can manually copy your public key to the remote server’s authorized keys file. However, ssh-copy-id offers a more convenient and secure method.
Q: Can I use ssh-copy-id with multiple remote systems?
A: Yes, you can use ssh-copy-id to add your public key to multiple remote systems. Simply run the command for each system you wish to connect to.
Tips for Secure SSH Connections
- Use strong passwords: If you must use password authentication, ensure that your passwords are complex and difficult to guess.
- Enable SSH key authentication: Prioritize public-key authentication for enhanced security.
- Keep your keys secure: Protect your private key file from unauthorized access.
- Update your SSH software: Regularly update your SSH client and server software to benefit from security patches.
- Restrict access: Configure SSH server settings to limit access to authorized users and networks.
Conclusion
ssh-copy-id is a valuable tool for establishing secure SSH connections in Windows 11. By automating the process of adding your public key to a remote server’s authorized keys file, it streamlines setup, enhances security, and improves overall efficiency. By understanding the principles of public-key authentication and utilizing ssh-copy-id, users can confidently navigate the complexities of secure remote access, ensuring secure and reliable communication with remote systems.



Closure
Thus, we hope this article has provided valuable insights into Navigating Secure Connections: A Comprehensive Guide to SSH in Windows 11. We thank you for taking the time to read this article. See you in our next article!
