Unraveling Your Digital Identity: A Comprehensive Guide to the "whoami" Command in Windows 11
Related Articles: Unraveling Your Digital Identity: A Comprehensive Guide to the "whoami" Command in Windows 11
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unraveling Your Digital Identity: A Comprehensive Guide to the "whoami" Command in Windows 11. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unraveling Your Digital Identity: A Comprehensive Guide to the "whoami" Command in Windows 11
![PowerShell Get Current Username on Windows 11/10/8/7 [Full Guide] - MiniTool Partition Wizard](https://www.partitionwizard.com/images/uploads/articles/2023/01/powershell-get-current-username/powershell-get-current-username-6.png)
In the intricate world of operating systems, understanding your digital footprint is paramount. Windows 11, with its focus on user-friendliness and security, provides a powerful command-line tool – "whoami" – that allows users to delve into the very core of their system identity. This article aims to demystify the "whoami" command, elucidating its functionalities, benefits, and applications in a clear and comprehensive manner.
Understanding the "whoami" Command
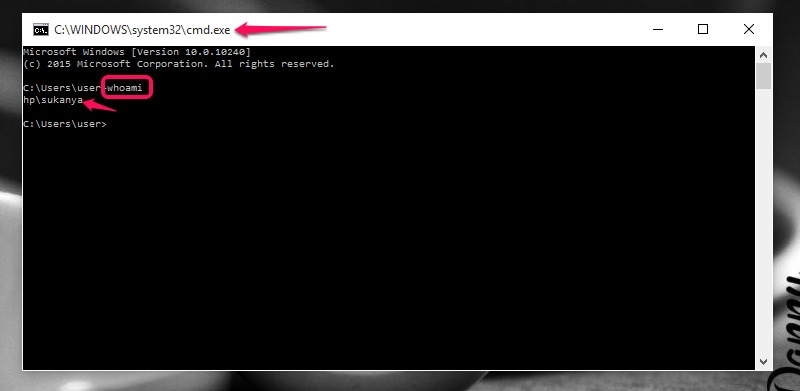
At its core, "whoami" is a simple yet invaluable command that reveals the current user’s security context. It provides a succinct snapshot of your system identity, including the username, domain, and security groups you are associated with. This information is critical for understanding your privileges, access rights, and overall system interaction.
The Mechanics of "whoami"
The "whoami" command operates by querying the system’s security database, retrieving relevant information about the currently logged-in user. This data is then presented in a concise and readily interpretable format. Typically, the output of "whoami" displays the following:
- Username: This is the unique identifier assigned to your user account.
- Domain: For networks with multiple users and computers, this indicates the domain to which your account belongs.
- Security Groups: These are collections of users with shared access rights and permissions.
Practical Applications of "whoami"
The "whoami" command proves invaluable in a multitude of scenarios, offering insights into your system’s security posture and aiding in troubleshooting various issues. Here are some notable applications:
- Understanding Permissions: By revealing the security groups you belong to, "whoami" helps you determine the permissions granted to your user account. This knowledge is crucial for navigating file access, program execution, and other system interactions.
- Troubleshooting Access Issues: If you encounter problems accessing specific files, folders, or programs, the "whoami" command can shed light on the underlying permissions that might be preventing access.
- Security Auditing: "whoami" provides a quick and easy way to check your current login status and confirm that you are indeed logged in as the intended user. This is particularly useful for verifying system security and identifying potential unauthorized access attempts.
- Scripting and Automation: The output of "whoami" can be incorporated into scripts and automation tasks, allowing for dynamic user identification and customized actions based on user context.
Beyond the Basics: Exploring Advanced Usage
While the basic "whoami" command offers valuable information, advanced options allow for more granular insights and tailored outputs. These options can be used in conjunction with the "whoami" command to extract specific details or tailor the output to your needs.
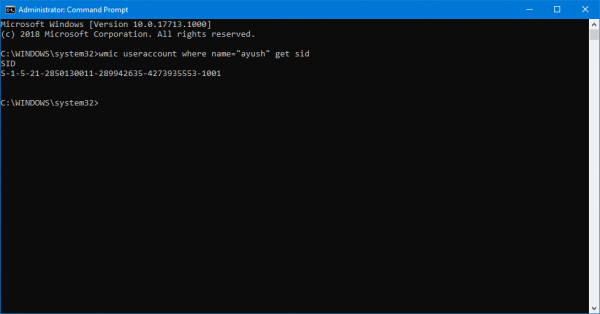
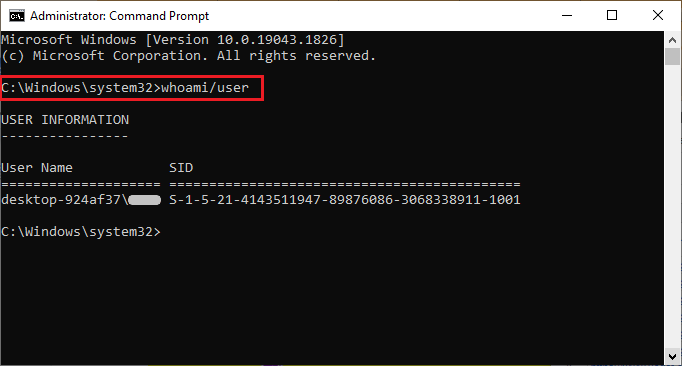
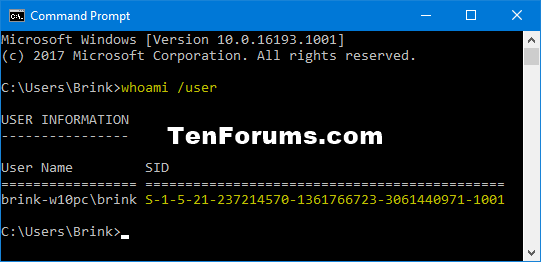
- "/user" Option: This option displays the user’s SID (Security Identifier), a unique and persistent identifier assigned to each user account. SIDs are used internally by the operating system to distinguish users and control access rights.
- "/groups" Option: This option provides a detailed listing of all security groups the user belongs to, including their names and SIDs. This information is particularly helpful for understanding the user’s permissions and access rights within the network.
- "/fqdn" Option: This option displays the fully qualified domain name (FQDN) of the user’s domain, providing a more comprehensive and unambiguous identification of the network environment.
FAQs: Addressing Common Questions about "whoami"
Q: What if "whoami" shows an unexpected username?
A: If "whoami" displays a username different from the one you expect, it indicates a potential security breach. It is crucial to investigate this discrepancy immediately, ensuring that your account has not been compromised.
Q: Can "whoami" be used to identify other users on the network?
A: No, "whoami" only provides information about the currently logged-in user. It cannot be used to identify other users on the network.
Q: Is "whoami" a replacement for other security tools?
A: "whoami" is a powerful tool, but it is not a replacement for comprehensive security measures. It provides a snapshot of your current security context, but it does not offer a complete picture of your system’s security posture.
Q: What are the security implications of using "whoami"?
A: The "whoami" command itself is not inherently insecure. However, it is important to be aware of the information it reveals and to use it responsibly. Avoid sharing the output of "whoami" with unauthorized individuals, as it could potentially compromise your system security.
Tips for Effective "whoami" Usage
- Use "whoami" regularly: Incorporate "whoami" into your regular system checks to ensure that your login status and permissions are as expected.
- Combine "whoami" with other commands: Leverage the power of "whoami" by integrating it with other command-line tools to perform complex tasks and gather more comprehensive information.
- Document your findings: Record the output of "whoami" for future reference, especially when troubleshooting access issues or investigating security concerns.
- Stay informed about security updates: Regularly update your operating system and security software to mitigate potential vulnerabilities and ensure the integrity of your system identity.
Conclusion: Embracing the Power of "whoami"
The "whoami" command in Windows 11 provides a valuable tool for understanding your digital identity and navigating the intricacies of system permissions and security. By leveraging its capabilities, users can gain valuable insights into their system’s security posture, troubleshoot access issues, and ensure a secure and efficient computing experience. As technology evolves, embracing command-line tools like "whoami" empowers users to take control of their digital environment and navigate the ever-evolving landscape of cybersecurity.


Closure
Thus, we hope this article has provided valuable insights into Unraveling Your Digital Identity: A Comprehensive Guide to the "whoami" Command in Windows 11. We appreciate your attention to our article. See you in our next article!
