windows 11 without tpm 2.0 and secure boot
Related Articles: windows 11 without tpm 2.0 and secure boot
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to windows 11 without tpm 2.0 and secure boot. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Windows 11 Landscape: A Comprehensive Guide to Operating Without TPM 2.0 and Secure Boot
Microsoft’s Windows 11 release ushered in a new era of security and performance enhancements. At the forefront of these improvements were two key features: Trusted Platform Module (TPM) 2.0 and Secure Boot. These features, while designed to bolster system security, have presented challenges for users with older hardware lacking these functionalities. This article aims to illuminate the complex landscape of Windows 11 without TPM 2.0 and Secure Boot, providing a comprehensive understanding of the implications, workarounds, and considerations involved.
Understanding the Security Landscape: The Importance of TPM 2.0 and Secure Boot
TPM 2.0 and Secure Boot are integral components of modern system security, acting as guardians against malicious software and unauthorized access. TPM 2.0, a dedicated security chip embedded in the motherboard, provides a hardware-based platform for encryption keys and secure authentication. It safeguards sensitive data, preventing unauthorized access even if the operating system is compromised.
Secure Boot, on the other hand, functions as a gatekeeper, ensuring that only trusted software, verified by a digital signature, can load during the system startup process. This effectively prevents boot-level malware from infiltrating the system and compromising its integrity.
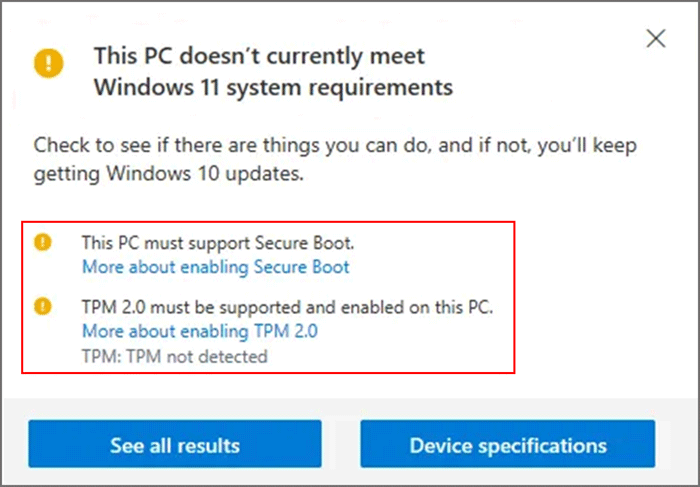
The Challenge of Legacy Hardware: Windows 11 and the Absence of TPM 2.0 and Secure Boot
While Windows 11 offers a host of new features and enhancements, its strict hardware requirements, including the mandatory presence of TPM 2.0 and Secure Boot, have excluded many users with older systems. This has sparked considerable debate and frustration, with users facing the dilemma of either upgrading their hardware or potentially compromising their system’s security.
Workarounds and Alternatives: Bypassing the Windows 11 Requirements
For users determined to install Windows 11 on systems lacking TPM 2.0 and Secure Boot, several workarounds and alternative methods exist. However, it is crucial to understand that these methods circumvent the security measures implemented by Microsoft and may expose the system to increased vulnerabilities.
1. Registry Modification: A common workaround involves manually modifying the Windows registry to bypass the TPM 2.0 and Secure Boot checks. This approach requires advanced technical knowledge and carries a significant risk of system instability or damage if performed incorrectly.
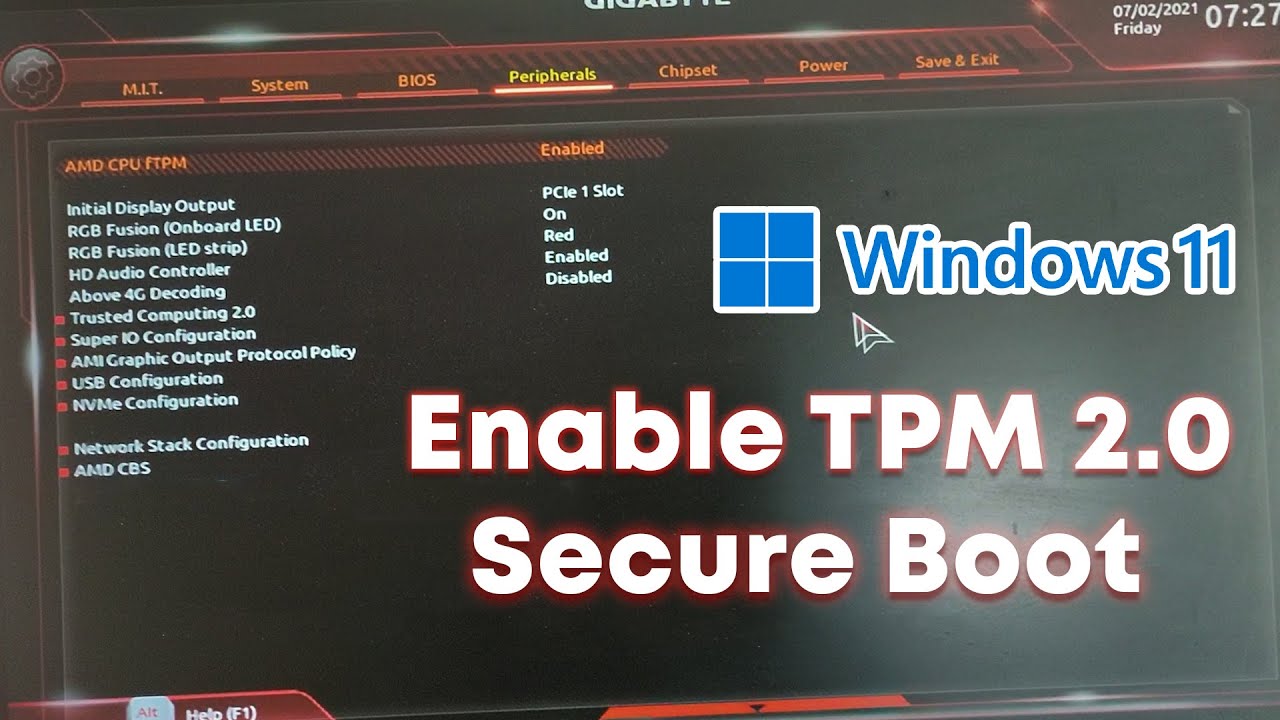
2. Disabling Secure Boot in BIOS: Disabling Secure Boot in the BIOS settings is another option, but it significantly reduces the system’s security posture. This approach should only be considered as a last resort, with the understanding that it compromises the system’s ability to verify the authenticity of boot components.
3. Using Third-Party Software: Certain third-party software solutions claim to enable Windows 11 installation without TPM 2.0 and Secure Boot. However, the legitimacy and security of these solutions should be carefully scrutinized, as they may introduce vulnerabilities or compromise the system’s integrity.
The Risks and Considerations: Operating Windows 11 Without TPM 2.0 and Secure Boot
Bypassing the TPM 2.0 and Secure Boot requirements comes with inherent risks, exposing the system to various security threats. These include:
- Malware Infection: Without Secure Boot, the system becomes susceptible to boot-level malware, which can gain control over the system before the operating system even loads.
- Data Compromise: TPM 2.0’s absence weakens the system’s ability to protect sensitive data from unauthorized access, increasing the risk of data breaches and theft.
- System Instability: Modifying the registry or disabling Secure Boot can potentially lead to system instability, crashes, or other malfunctions.
- Security Updates and Compatibility: Operating without TPM 2.0 and Secure Boot may limit access to future security updates and compatibility with newer software and hardware.
The Importance of Security: A Balanced Approach
While the desire to upgrade to Windows 11 is understandable, prioritizing system security should remain paramount. For users with legacy hardware lacking TPM 2.0 and Secure Boot, it is advisable to consider alternative solutions, such as:
- Upgrading to a Newer System: The most secure and reliable option is to upgrade to a system that meets Windows 11’s hardware requirements, ensuring compatibility with TPM 2.0 and Secure Boot.
- Remaining on Windows 10: Windows 10 continues to receive security updates and support, offering a stable and secure platform for users with older hardware.
- Exploring Other Operating Systems: Linux distributions, known for their security focus, provide viable alternatives for users seeking a secure and feature-rich operating system.
FAQs: Addressing Common Questions
1. Is it safe to use Windows 11 without TPM 2.0 and Secure Boot?
No, it is not safe. Operating without TPM 2.0 and Secure Boot significantly compromises the system’s security, making it vulnerable to malware, data breaches, and other threats.
2. What happens if I disable Secure Boot?
Disabling Secure Boot weakens the system’s ability to verify the authenticity of boot components, increasing the risk of malware infection and system instability.
3. Can I enable TPM 2.0 on my older system?
TPM 2.0 is a hardware component embedded in the motherboard. It cannot be enabled on systems that lack this chip.
4. What are the alternatives to Windows 11?
Windows 10 continues to receive security updates and support, while Linux distributions provide secure and feature-rich alternatives.
5. Is it possible to install Windows 11 without TPM 2.0 and Secure Boot using a USB drive?
While it may be possible to install Windows 11 without TPM 2.0 and Secure Boot using a USB drive, it is not recommended due to the significant security risks involved.
Tips for Users with Legacy Hardware:
- Prioritize Security: Understand the risks involved in operating without TPM 2.0 and Secure Boot and make informed decisions regarding system security.
- Explore Alternatives: Consider upgrading to a newer system, staying on Windows 10, or exploring alternative operating systems like Linux.
- Stay Informed: Keep abreast of security updates and vulnerabilities to mitigate potential risks.
- Use Antivirus Software: Utilize reputable antivirus software to protect against malware threats.
- Practice Safe Computing Habits: Follow best practices for online security, such as using strong passwords, avoiding suspicious websites, and keeping software up to date.
Conclusion:
The decision to operate Windows 11 without TPM 2.0 and Secure Boot is a complex one, requiring a careful balance between functionality and security. While workarounds and alternatives exist, it is crucial to acknowledge the inherent risks involved. Users with legacy hardware should prioritize system security, exploring alternative solutions that prioritize stability and protection against potential threats. Ultimately, the choice rests with the user, who must weigh the benefits and drawbacks of each option to make an informed decision that aligns with their individual needs and priorities.





Closure
Thus, we hope this article has provided valuable insights into windows 11 without tpm 2.0 and secure boot. We appreciate your attention to our article. See you in our next article!
